Risk assessments are not one-and-done checkboxes—they are the backbone of effective risk management. Frameworks like ISO 31000 and NIS2 emphasize that risk assessments should be ongoing, dynamic, and embedded in decision-making. In today’s volatile business environment, organizations cannot rely solely on static annual reviews. They must reassess risks whenever significant changes occur.
For financial services risk managers, compliance officers, and technology executives, timing is critical. Below, we explore six enterprise-critical moments when conducting a fresh risk assessment is imperative—anchored in best practices from Basel III, DORA, and global governance standards.
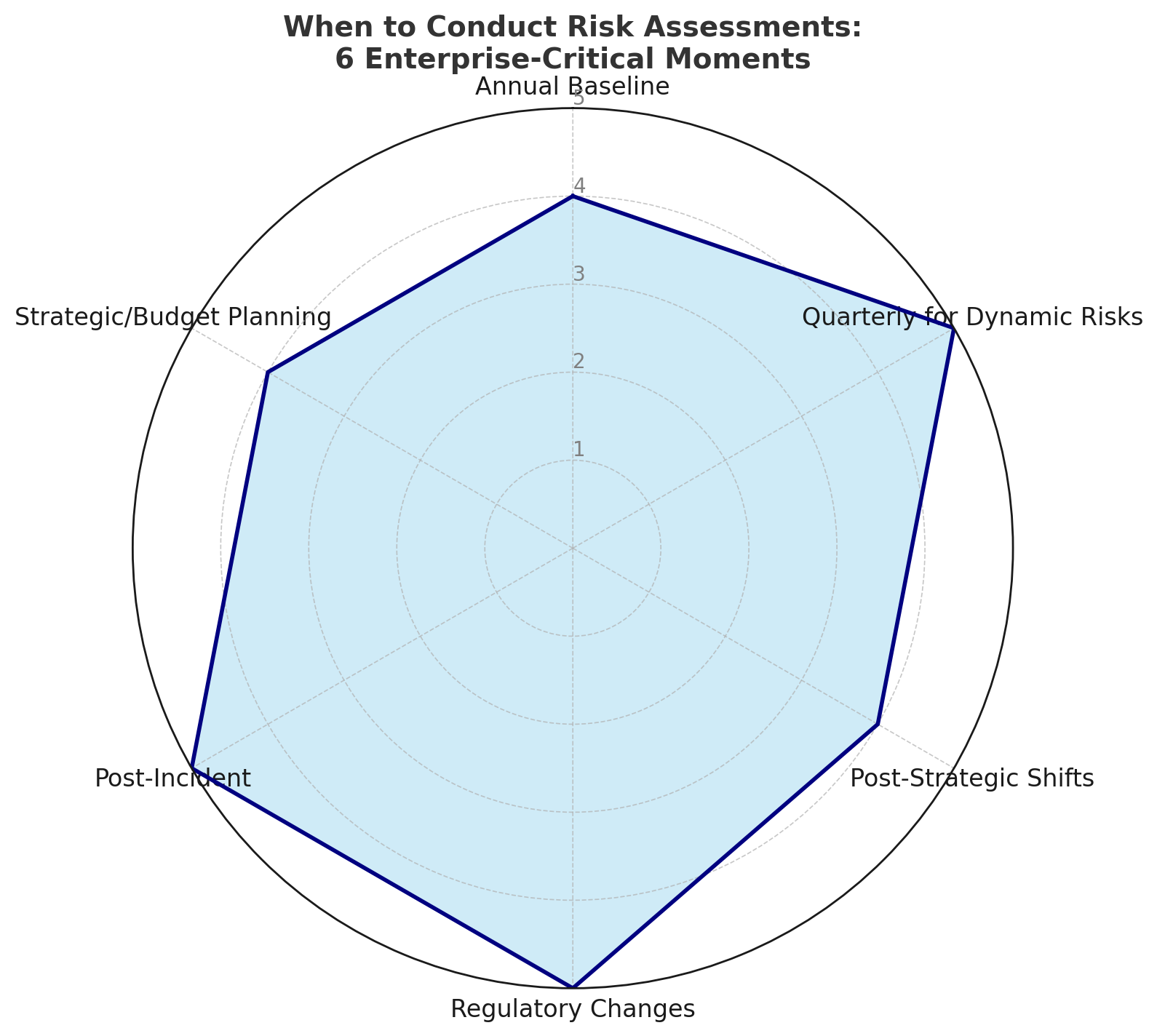
1. At Minimum: Annually for Baseline Compliance
Regulators across the globe expect an annual, enterprise-wide risk assessment. Supervisory authorities under Basel III, as well as local regulators like DNB and AFM, treat annual reviews as a baseline obligation. These reviews establish a documented risk profile, validate alignment with your risk appetite, and provide audit evidence.
Yet relying solely on annual cycles is dangerous. A full year can leave your organization blind to fast-emerging threats. In cybersecurity, third-party management, and financial crime, risk profiles shift too quickly for annual check-ins. An annual assessment sets the foundation, but forward-looking organizations reinforce it with quarterly and ad-hoc reviews.
2. Quarterly (or More) for Dynamic Risk Areas
Some areas change too quickly to leave unexamined for a year. These require quarterly—or even monthly—assessments:
- Cybersecurity & Information Security – vulnerabilities and threat actors evolve daily. Both NIST and ISO 27001 call for ongoing monitoring, not one-time audits.
- AML & Fraud – fraud typologies shift constantly; monitoring controls must be retuned frequently.
- Critical Third-Party Vendors – particularly ICT providers. Under DORA, financial institutions must continuously monitor outsourced partners.
- IT Change Management – migrations, upgrades, and DevOps releases bring volatility; assessments should precede and follow significant changes.
The logic is clear: it’s better to detect a risk escalation now than to face regulatory findings or a breach six months later.
3. Immediately After Organizational or Strategic Shifts
Strategic and structural changes reshape risk overnight. Trigger a reassessment whenever:
- Mergers & Acquisitions – combined entities inherit each other’s risks; integration exposes new gaps.
- New Products or Markets – bring unfamiliar processes and regulatory regimes.
- Infrastructure or Cloud Migrations – a “major ICT change” under DORA requires mandatory reassessment.
- Leadership or Org Changes – shifts in accountability can leave risks without clear ownership.
Every one of these materially alters your control landscape. Immediate reassessment provides the fresh lens needed to realign exposures and controls.
4. In Response to Regulatory Change
The risk landscape is shaped not just by your business, but by regulators. When rules or standards evolve, risk assessments must follow:
- New/Updated Laws – such as DORA for ICT resilience, GDPR/CCPA for privacy, or ESG disclosure rules.
- Regulatory Guidance – supervisors like DNB, AFM, or ESMA often issue new expectations on cyber resilience, outsourcing, or climate risk.
- Framework Updates – revisions to ISO 31000, NIST, or COSO ERM should trigger reviews to keep your approach state-of-the-art.
Updating assessments in step with regulation ensures compliance, avoids audit findings, and can even create competitive advantage by addressing emerging focus areas early.
5. Post-Incident or Control Failure
Incidents expose blind spots that traditional assessments may have missed. A major breach, data loss, compliance violation, or audit finding should trigger an immediate reassessment to:
- Re-evaluate likelihood and impact based on real evidence.
- Identify control gaps and recalibrate mitigation.
- Document lessons learned to strengthen institutional memory.
Regulators increasingly expect post-incident assessments as part of remediation. More importantly, capturing these learnings ensures resilience grows with every challenge.
6. During Strategic or Budget Planning
Risk appetite must align with strategy and resource allocation. Reassess risks as part of:
- Annual strategy reviews – boards increasingly demand updated risk profiles alongside business plans.
- Budgeting and investment cycles – high-risk initiatives require proportionate controls and funding.
- Transformation programs – digital, operational, or cultural shifts change exposures across people, process, and technology.
This ensures plans are grounded in risk reality, preventing over-optimism and aligning capital with the areas of greatest exposure.
What Happens If You Delay or Deprioritize Assessments
Postponing or ignoring these critical risk assessment moments can seriously erode your risk oversight and effectiveness. Some of the consequences of a lax risk assessment cadence include:
- Outdated Risk Profiles: You end up making decisions based on stale data. Threats, business processes, and controls might have changed since the last assessment, meaning your current risk register is no longer accurate. For example, one study found that many organizations not doing frequent assessments operate with outdated risk profiles that would fail under serious audit scrutiny. Essentially, you’re flying blind with an old map.
- Audit and Regulatory Gaps: If you miss required assessments or let risk documentation lapse, auditors and regulators will notice. Gaps in your risk assessment history (e.g. an area that hasn’t been reviewed in 2+ years) are red flags. Regulators could cite you for failing to follow guidelines (like those under Basel or local regulations), and auditors may issue findings for “lack of risk assessment of X area.” Moreover, without up-to-date assessments, you might be out of compliance with new rules (since you haven’t evaluated against them). This can lead to unpleasant surprises during exams.
- Lack of Ownership and Accountability: Regular risk reviews keep management attention and ownership fresh. If assessments are delayed indefinitely, accountability for certain risks can fade – people assume “no news is good news.” Business units may not feel responsible for managing a risk if it hasn’t been discussed or updated in years. Over time, risk governance becomes ineffective as no one can clearly articulate who is responsible for what. The tone at the top also suffers, as infrequent risk review signals that leadership doesn’t truly prioritize risk management beyond lip service.
- Control Drift: In the absence of periodic check-ins, mitigation measures can drift away from their intended performance. Controls that were implemented last year might become less effective due to process changes, resource attrition, or simple entropy. Without testing and re-assessment, you won’t notice that drift until a control fails. Continuous monitoring is meant to catch control failures or lapses before an incident or audit occurs. If you’re not assessing regularly, controls could be “off the rails” for a long time, undermining your risk posture. This also creates “audit fatigue” when you finally do assess, because so many issues have piled up unaddressed.
- Operational Blind Spots: Perhaps most importantly, a delayed assessment cadence means you miss early warning signs. Today’s business and threat environment changes rapidly; new risks emerge quickly. If you’re not actively looking, you won’t see them until they hit you. This blind spot can be fatal for operations. (Think of companies that missed the shift to remote work risks before COVID-19, or banks that ignored mounting liquidity risks before a crisis.) As AuditBoard notes, failing to update risk assessments multiple times a year can result in “missing emerging risks that may disrupt business objectives”. In other words, you’re reactive, always a step behind emerging challenges.
In short, complacency in risk assessment is itself a risk. It leads to outdated assumptions, weak oversight, and nasty surprises. Conversely, a proactive cadence protects the organization by keeping risk knowledge current and actionable.
Best Practices: Building a Risk-Aware Cadence
- Establish Tiered Review Frequencies
Not all risks require the same cadence. Match review cycles to the criticality of each domain: quarterly for high-risk areas, annually for lower-tier domains.
- Define Trigger Events
Codify internal and external changes that mandate reassessment—such as product launches, vendor switches, system migrations, or leadership changes.
- Automate Reminders
Manual tracking introduces risk. Use a GRC platform to manage timelines, assign responsibilities, and enforce evidence requirements.
- Centralize Evidence
A fragmented audit trail undermines credibility. Maintain a digital repository of risk decisions, control updates, and reassessment logs.
- Integrate with Governance Reviews
Risk data shouldn’t sit in silos. Present updated risk snapshots at board, audit committee, and strategic planning sessions to embed accountability across functions.
How CERRIX Enables Adaptive Risk Reassessment
CERRIX transforms risk assessment into an adaptive, evidence-driven discipline:
- Collaborative input – Forms module engages stakeholders across functions.
- Risk register as single source of truth – covering strategic, operational, ICT, and third-party risks.
- Trigger-based workflows – incidents, vendor changes, or ICT migrations auto-initiate reassessments.
- Dashboards and KPIs – track risk trends, appetite alignment, and process health.
- Audit-ready documentation – full traceability for ISO 31000, NIST, Basel, and DORA compliance.
With CERRIX, risk management become continuous, automated, and embedded in decision-making—freeing teams from manual chasing while strengthening resilience and compliance.
From Fragmented Risk Data to Integrated Risk Management
Accessible popup
Welcome to Finsweet's accessible modal component for Webflow Libraries. This modal uses custom code to open and close. It is accessible through custom attributes and custom JavaScript added in the embed block of the component. If you're interested in how this is built, check out the Attributes documentation page for this modal component.

.jpg)
%20(3).jpg)

.jpg)
%20(1).jpg)
.jpg)
.jpg)
.jpg)
.jpg)
%20(1).jpg)
.jpg)
%20(1).jpg)
.jpg)
.jpg)

.jpg)





.jpg)

%20(2).jpg)
















%20(1)%20(2).jpg)





.jpg)

.png)
.jpg)






%20(1).avif)



