Writing a strong incident report is about more than documenting what went wrong. In regulated industries—like financial services, healthcare, or critical infrastructure—it’s about creating a traceable, structured account that can satisfy internal review, external audits, and even regulators.
While most teams understand the basics of incident reporting, many still struggle to write reports that hold up under scrutiny. Vague descriptions, missing timestamps, or unclear remediation plans are common pitfalls. The real challenge is balancing speed, completeness, and audit-readiness.
In this article, we’ll explore how to write incident reports that stand up to audits, align with compliance frameworks like ISO 27001 and GDPR, and integrate with your broader governance, risk, and compliance (GRC) strategy.
What Makes an Incident Report Audit-Ready?
An audit-ready incident report goes beyond surface documentation. It tells a complete story, backed by timestamps, structured ownership, and traceable evidence. At a minimum, each report should include the following elements:
- When the incident occurred and was detected, including exact time and context
- Who was involved, from the reporter to the responsible party managing resolution
- What exactly happened, described clearly and factually without guesswork
- Why it happened, with an honest analysis of contributing factors and control gaps
- What was done about it, including immediate mitigation and long-term corrective actions
What separates a good report from a great one is not just structure, but alignment. The report must connect back to your organization’s controls, risks, and governance processes.
Writing Strong Narrative Sections: What to Include and Why It Matters
Even sophisticated teams make simple reporting mistakes that weaken audit integrity. Avoid these common pitfalls:
- Vague Descriptions: “The system went down” isn’t enough. Use structured narrative, not emotion.
- Delayed Logging: Reporting days or weeks later increases error and weakens credibility.
- No Assigned Owners: Incidents without responsibility get lost in the shuffle.
- Offline/Email-Based Reports: You lose version control, traceability, and audit trail.
- No Link to Risk or Controls: Standalone incidents can’t inform governance.
When writing the core narrative of an incident report, clarity is key. A good description avoids jargon or vague terms like “user mistake” or “unknown error.” Instead, focus on sequencing—what happened, when, and how it was discovered. Mention any systems, teams, or third parties involved.
Let’s break this down using an example.
Instead of:
“There was an issue with the server on Monday.”
Use:
“At 09:45 on 23 September, the CRM production server became unresponsive due to a failed software patch deployment initiated by IT Ops. The incident was detected within 5 minutes by the network monitoring team and escalated to the IT Security lead.”
This revised version captures time, context, system impacted, and escalation—all elements required for audit credibility.
5 Elements of an Audit-Ready Incident Report
Audit-worthy incident reports are clear, standardized, and backed by evidence. Here's what every report must include—and why it matters:
From Templates to Transformation: Why GRC Platforms Like CERRIX Are the Better Way to Report Incidents
Excel or Word templates can work well in the early stages of an incident reporting program. They’re quick to spin up and easy to distribute across teams. But as incident volume grows—or when regulatory scrutiny increases—these static tools start to fall short. Without automated routing, version control, or integrated risk mapping, templates often lead to lost context, delayed responses, and weak audit readiness.
CERRIX offers a modern alternative: a structured, workflow-driven approach where incidents are logged, assigned, and escalated in real time. Each report is embedded in the broader GRC environment—linked to risks, controls, affected systems, and third parties. The platform automates follow-ups, tracks remediation, and provides full audit trails with role-based permissions.
For teams operating in regulated sectors or aligning to ISO 27001, CERRIX isn’t just more efficient—it’s transformative. It turns incident reporting from a compliance checkbox into a live, transparent process that builds trust, resilience, and operational control.
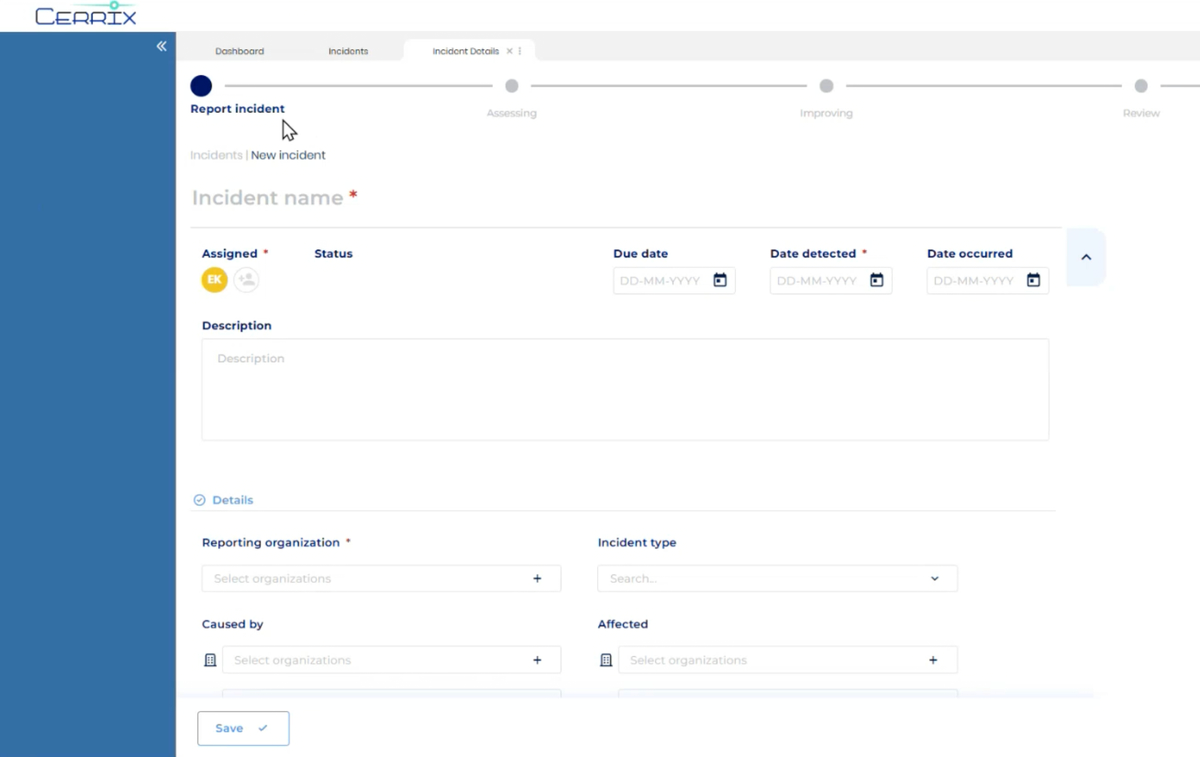
Tying the Incident to Risk and Controls
Too often, incident reports live in isolation. But without connecting the report to your control framework or risk register, it becomes harder to learn from the event.
Let’s say a phishing attack bypasses email filters and tricks an employee into sharing login credentials. The incident report should not only describe the event—it should also:
- Reference the control(s) that failed or were missing
- Highlight which risk category it falls under (e.g., social engineering, access control)
- Include a recommendation for improving controls or awareness training
In platforms like CERRIX, this linkage can be done automatically by tagging controls or risks within the incident module. This transforms the report from a standalone document into part of your compliance and risk management system.
Scaling Incident Reporting Across Teams
Small teams may start with spreadsheets or basic forms—but this approach becomes unsustainable fast. That’s why GRC platforms like CERRIX offer scalable workflows that ensure:
- Incident data is complete and comparable across business units
- Owners are assigned and reminded automatically
- Reports are version-controlled and audit-traceable
- Incidents are embedded in broader control and risk strategies
Whether you're managing 10 or 100 incidents per year, this structured approach eliminates the risk of things slipping through the cracks.
Final Thoughts: Turn Incident Reporting Into a Strength
When treated as a strategic capability, incident reporting becomes more than reactive documentation. It’s a driver of visibility, accountability, and operational improvement.
Audit-ready reports help surface weak points in your controls, improve cross-functional collaboration, and feed into continuous improvement cycles. They also prove—beyond a doubt—that your organization is in control.
By integrating platforms like CERRIX, you can turn this process from a patchwork effort into a structured, resilient workflow that meets regulatory expectations and internal demands.
Audit Management: Aligning the Three Lines of Defense
Accessible popup
Welcome to Finsweet's accessible modal component for Webflow Libraries. This modal uses custom code to open and close. It is accessible through custom attributes and custom JavaScript added in the embed block of the component. If you're interested in how this is built, check out the Attributes documentation page for this modal component.

.jpg)
%20(3).jpg)

.jpg)
%20(1).jpg)
%20(1).jpg)
.jpg)
.jpg)
.jpg)
%20(1).jpg)
.jpg)
.jpg)
.jpg)

.jpg)
.jpg)






%20(1).avif)



