For decades, control assurance has been dominated by effectiveness testing. Organizations assess whether controls worked as intended over a past period, typically aligned with the annual external audit cycle. This backward-looking approach made sense in a world where assurance was periodic, manual, and audit-driven.
But the way organizations manage risk has evolved. Digital processes, regulatory expectations, and management accountability increasingly demand forward-looking assurance, not just retrospective validation.
To understand this shift, let’s first revisit the full lifecycle of a control.
The Control Lifecycle: Four Interconnected Phases
When examined holistically, control assurance consists of four distinct, but interdependent phases:
- Design & Implementation
- Control Execution
- Effectiveness Testing
- Audit & Assurance

Each phase answers a different assurance question. Together, they determine whether controls genuinely support risk management rather than merely satisfy audit requirements.
Design& Implementation: The Foundation of Any Control
The first phase focuses on design and implementation. This phase assesses whether a control is capable of mitigating its associated risk and whether it has been properly embedded in the organization.
Two dimensions are assessed separately:
- Design – Is the control logically structured to mitigate the identified risk?
- Implementation – Is the control formally documented, communicated, and put into operation?
This phase is most commonly applied when establishing or updating a control framework. Responsible managers or employees are asked to provide evidence that controls have been implemented as intended. Once successfully assessed, a control can be classified as “implemented.”
From a governance perspective, this phase is non-negotiable: A control that is poorly designed or not implemented can not be meaningfully executed or tested for effectiveness.
A well-executed design and implementation assessment typically answers questions such as:
- Does the control still mitigate the linked risk?
- Is the control described as it is actually performed in practice?
- Does the description meet the standards of a good control definition (the 5 W’s and H)
Typical evidence includes:
- Policy and procedure documentation
- System configurations
- Proof of implementation
- Communication and training materials
Only once this foundation is in place does control execution become meaningful.
Control Execution: Where Assurance Moves into the Business
Control execution refers to the actual performance of a control, by people, systems, or a combination of both, according to its defined frequency and procedure.
Historically, controls were executed, but execution evidence was fragmented. Documentation was scattered across emails, shared drives, local folders, or not retained at all. As a result, management had limited visibility, and assuranceactivities remained labor-intensive.
Today, control execution is increasingly recognized as a first-line responsibility. Managers are accountable not only for risks, but also for ensuring that controls are executed consistently and transparently.
Controls may be:
- Manual
- Semi-automated
- Fully automated
Each brings its own challenges. Decentralized evidence storage makes oversight difficult, particularly for second-line functions assessing operating effectiveness.
A clear best practice has emerged: Centralize control execution and evidence.
Doing so simplifies work for control owners, improves transparency for management, and enables earlier detection of issues, allowing organizations to address weaknesses before they escalate.
Watch the webinar ISO 27001 Control Automation: From Control Execution to Continuous Assurance
Automated Controls: Opportunity Comes with Preconditions
Automated controls, such as IT General Controls (e.g. access management, change management) or application controls(e.g. enforced workflows, mandatory fields), offer significant potential for continuous assurance.
However, automation alone does not guarantee reliable evidence.
In practice, organizations often encounter barriers such as:
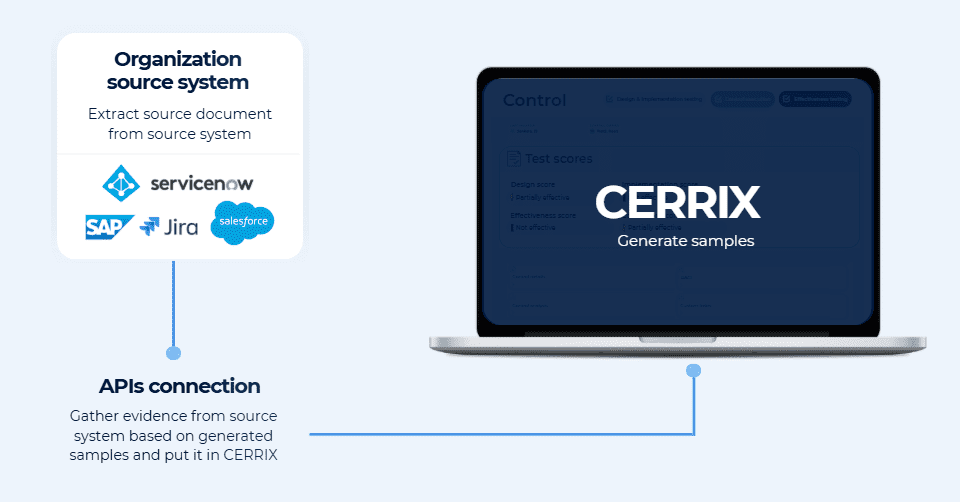
- Limited data availability – Control data cannot be easily extracted from source systems
- Data quality issues – Incomplete or inconsistent data undermines reliability
- Insufficient logging and monitoring – Common in legacy environments
- Weak control descriptions – Lack of standardization creates misalignment between expected and actual evidence
Without addressing these prerequisites, continuous control monitoring remains aspirational rather than achievable.
To support this, CERRIX introduced Execution-Based Control Testing. Automated controls can expose their execution results via the Control Execution API, allowing near-real-time capture of execution data directly from source systems. These execution records are then reused for effectiveness testing through automated sampling and review workflows, without relying on screenshots or manually prepared population files.
By linking automated executions directly to effectiveness testing, CERRIX enables continuous insight into control operation while preserving audit trails and expert judgement. Automation therefore strengthens assurance reliability rather than merely accelerating testing activities.
Effectiveness Testing: Still Relevant, but No Longer Sufficient
Effectiveness testing remains the most familiar phase of control assurance. Traditionally, assurance programs relied heavily on periodic tests that looked back over a defined period, mirroring the approach of internal and external audits.
Effectiveness testing answers a critical question: Did the control actually work?
But this assessment is only meaningful if:
- Control execution is properly documented
- Evidence is reliable, complete, and traceable
Modern approaches increasingly support automated effectiveness testing, including:
- Sampling based on execution data
- Direct links to source systems
- Reduced reliance on manual evidence collection
-
This shifts effectiveness testing from a standalone exercise to a natural outcome of structured execution and monitoring.
Audit & Assurance
Audit &assurance form the final phase of the control lifecycle and provide independent validation that controls are designed, executed, and operating effectively. This role is typically fulfilled by internal audit, external auditors, or supervisors.
Historically, audit has driven control testing by looking back at a defined period. In a mature control assurance model, this dynamic changes: audit becomes a user of assurance outputs, not the driver of control execution or testing.
When control design, execution, and effectiveness testing are properly embedded and documented, audit can rely on existing evidence. This enables a shift from ad-hoc audit preparation to continuous audit readiness, reduces disruption to the business, and allows audit to focus on judgement, challenge, and improvement rather than reconstruction of evidence.
Audit & assurance therefore act as the closing loop in the control lifecycle, confirming that the organization is not only compliant, but demonstrably in control.
Conclusion: From Control Activities to Continuous Monitoring
Effective control assurance is not about performing more tests, it is about creating confidence through clarity, ownership, and quality.
- Design & Implementation provide the foundation: clean, reliable control frameworks that are clearly defined, consistently applied, and aligned with the risks they are meant to mitigate. Without this hygiene factor, assurance lacks credibility.
- Control Execution brings assurance into the business. By making execution transparent and structured, managers gain direct insight into how controls operate in practice. Control assurance becomes a management instrument, not an audit exercise.
- Effectiveness Testing adds professional judgement. Through expert review of execution data and evidence, organizations gain a cohesive and complete view of control performance, focused on quality, not volume.
Together, these values shift control assurance from a retrospective compliance activity to make it audit readiness day by day, one that supports informed decision-making, strengthens accountability, and builds lasting trust with internal and external stakeholders.
Blog author
Ruben Andeweg (Senior Risk Consultant, CERRIX)
GRC Maturity Assessment Guide
Accessible popup
Welcome to Finsweet's accessible modal component for Webflow Libraries. This modal uses custom code to open and close. It is accessible through custom attributes and custom JavaScript added in the embed block of the component. If you're interested in how this is built, check out the Attributes documentation page for this modal component.

%20(3).jpg)

.jpg)
%20(1).jpg)
.jpg)
.jpg)
.jpg)
.jpg)
%20(1).jpg)
.jpg)
%20(1).jpg)
.jpg)
.jpg)

.jpg)
.jpg)





.jpg)

%20(2).jpg)
















%20(1)%20(2).jpg)





.jpg)

.png)
.jpg)






%20(1).avif)



